Building Resilience: Strategies for Cybersecurity Risk Assessment
In an era where digital threats are omnipresent, conducting a comprehensive cybersecurity risk assessment is imperative for businesses. This article explores the importance of cybersecurity risk assessment, its key components, and strategies to fortify defenses against evolving cyber threats.
Cybersecurity Risk Assessment at BusinessInc.my.id
Discover the depth of cybersecurity risk assessment at BusinessInc.my.id. This platform exemplifies a commitment to robust cybersecurity practices, showcasing how businesses can navigate the complex landscape of digital risks and ensure the security of their digital assets.
Understanding Cybersecurity Risk Assessment: A Foundation of Defense
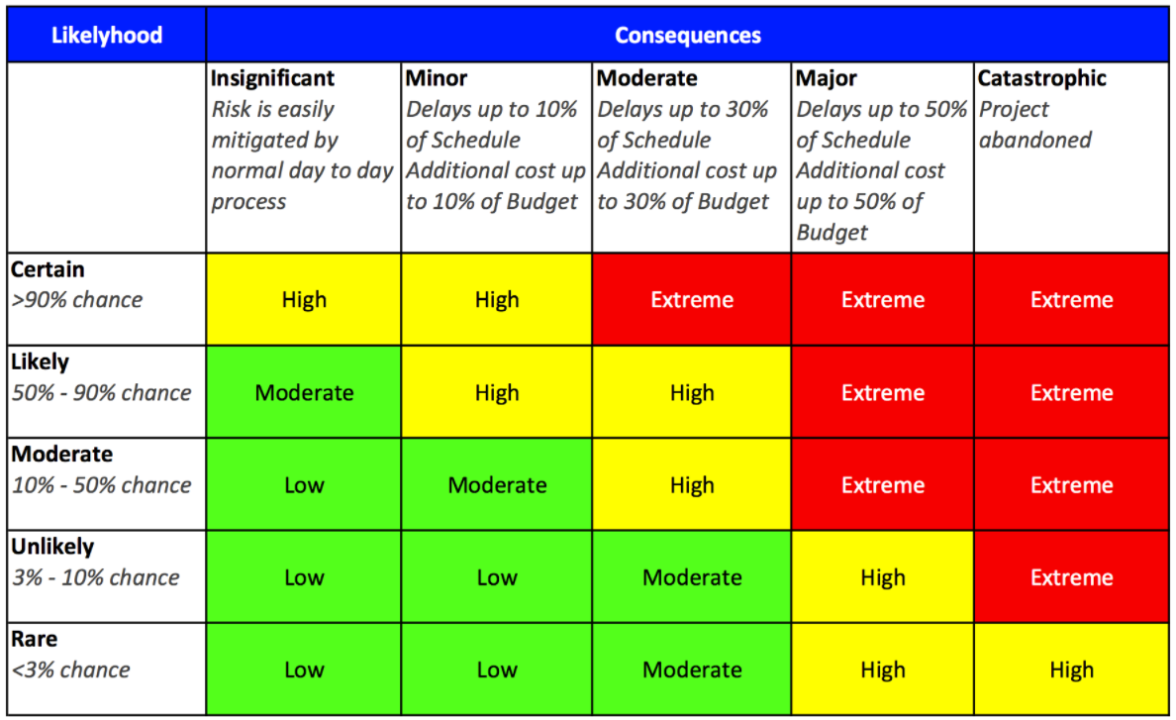
Cybersecurity risk assessment involves evaluating an organization’s digital landscape to identify vulnerabilities, potential threats, and the impact of a security breach. This foundational process forms the basis for designing and implementing effective cybersecurity measures tailored to an organization’s specific risk profile.
Identifying Assets and Establishing Risk Criteria
The first step in cybersecurity risk assessment is identifying digital assets critical to business operations. These assets can include sensitive data, intellectual property, customer information, and more. Establishing risk criteria involves determining the potential impact of threats on these assets.
Threat Identification and Classification: Knowing the Enemy
Thorough threat identification is central to a successful risk assessment. This involves recognizing and classifying potential threats such as malware, phishing attacks, data breaches, and other cyber threats. Understanding the nature of these threats is essential for developing targeted mitigation strategies.
Vulnerability Assessment: Assessing Weak Points
Conducting a vulnerability assessment involves identifying weaknesses in an organization’s systems, networks, and applications that could be exploited by cyber threats. This step is crucial for prioritizing vulnerabilities based on their potential impact and likelihood of exploitation.
Quantifying and Qualifying Risks: Balancing Act
Quantifying and qualifying cybersecurity risks is a balancing act that involves assigning values to potential risks based on their severity and probability. This process helps organizations prioritize risks and allocate resources efficiently to address the most critical threats to their digital infrastructure.
Risk Mitigation Strategies: Strengthening Defenses
Once risks are identified and assessed, organizations must develop and implement effective risk mitigation strategies. This may involve deploying security technologies, implementing best practices, enhancing employee training, and continuously monitoring and updating defenses to stay ahead of emerging threats.
Continuous Monitoring and Adaptation: A Dynamic Process
Cyber threats are dynamic, and cybersecurity risk assessment is an ongoing process. Continuous monitoring ensures that organizations stay vigilant against evolving threats. Regular assessments and adaptations to cybersecurity measures help maintain a proactive stance against the ever-changing threat landscape.
Employee Training and Awareness: A Human Firewall
Employees play a pivotal role in cybersecurity, and training them to recognize and respond to potential threats is critical. Establishing a culture of cybersecurity awareness turns employees into a human firewall, reinforcing the organization’s overall cybersecurity posture.
Incident Response Planning: Preparing for the Unthinkable
Despite robust preventive measures, no system is entirely immune to cyber threats. Developing an incident response plan is crucial for minimizing the impact of a security breach. This plan outlines the steps to take when a cybersecurity incident occurs, ensuring a swift and coordinated response.
Conclusion
In conclusion, cybersecurity risk assessment is not just a technical requirement; it is a strategic imperative for businesses operating in the digital age. As demonstrated by BusinessInc.my.id, organizations that prioritize and implement comprehensive cybersecurity risk assessment strategies fortify their defenses against the evolving landscape of cyber threats. By understanding risks, identifying vulnerabilities, and developing proactive mitigation strategies, businesses can navigate the digital realm with resilience and confidence.